|
Information Security Aligned To Enterprise
Management

Istikoma
Nurul Fahimah Bt Fakhri
Qurat-ul-Ain
Jamaludin Ibrahim
Kulliyah of Information Technology,
International Islamic University,
Malaysia
Correspondence:
Istikoma
Kulliyah of
Information Technology,
International Islamic University,
Malaysia
Email: jannahnaty@yahoo.com

Abstract
This paper illustrates business aligned
security approach as a key element
of an enterprises's overall business
strategy. Business information security
is a crucial concern in enterprise
management for risk handling operation.
Te modern era of technology security
for businesses is increasingly recognized
especially in business strategies.
Disconnection of information security
procedures and commercial strategic
business objectives effects to control
security spending and their risk,
incidents and losses. Operational
enterprise system requires aligning
security practices through embedding
information security risk management
into the organization, however it
faces major challenges to support
and enable the business. Alignment
security in business process is one
of the biggest challenges in good
organization as it needs support resources
and time management and ways to align
security to overcome business objectives.
Thus, an information security management
role is important as a guideline to
execute Business Information Security.
In addition, the systematic security
management introduces a business model
for critical information infrastructure
protection. Organization design and
strategy, people, process and technology
are the elements of the model which
play an effective role in information
security but it requires a balance
among them.
Key words: business aligned
security, enterprises overall business
strategy, business information security,
information security risk management,
information security management(ISM).

Introduction
Nowadays, the important of information
security in enterprise environment
has a huge impact. Information security
has become more crucial by most organizations
for risk mitigation action. The activity
of protecting business must be the
first and foremost of achievement
in any security program. This view
has been supported by the security
profession, security approaches and
government processes used. The information
security vocation grew out of the
review profession, compliance and
regulatory groups, and public security
agencies, which has the profession
as the risk-centric of security. Due
to some issues several enterprises
have not made it a core competency.
This is because the limitation of
organization must open the realization
for some organization as to the importance
of their security in order to achieve
business goals as vital and actively
engage business stakeholders in the
security issue. As a result it has
become an untied program, sluggish
and largely unsuccessful. Therefore,
there are many organization that need
to struggle to accomplish a crucial
alignment. Aligning security programs
with an enterprise needs a sturdy
understanding of the technical area
like how the diverse computing technologies
are positioned across the enterprise
and their business significance, in
addition, as to how the specific protection
supports precise business strategy
objectives. Accordingly, it has a
new approach to security governance
which can make the transformation
from information security risk function
to a business aligned competence and
help to see how security is viewed
and subsidized within the enterprise.
The effort to enhance focus on a business
aligned approach will uplift security
from a purely mitigation action to
a tactical business enabler for the
enterprise.
Project Background
The nature of business information
technology is at a crossroads. The
pressure to enforce good corporate
governance, secure sensitive information
and meet compliance mandates would
seem to demand ever-tighter controls.
On the other hand, the need to respond
to new business opportunities, to
collaborate with a greater number
of partners more closely, and the
emergence of new technologies are
placing unprecedented strain on existing
security processes and practices.
But main highlighting factor is to
elevate security from a purely risk
mitigation activity to a strategic
business enabler for enterprise management
system. The aim of the business aligned
security approach is to shape a security
strategy that supports and enhances
the operational efficiencies of business.
There is no single tactic or strategy
that guarantees success in improving
business alignment of security. It
is mandatory to understand the business
needs and leverage the security program
to increase operational efficiency,
safeguard users and information, make
the most of return on technology investment
and contain costs. Business aligned
security helps to protect business
from relevant threats and reduce risk,
and demonstrate a proactive posture
to safeguard critical assets and elevate
security from a tactical function
to a strategic business enabler.
The enterprise system aligned secure
business strategy may improve internal
process efficiencies, raise service
quality of enterprise management system
and reduce enterprise operational
risk threats. The business aligned
security approach assists risk tolerance
in the main crucial part of the enterprise
system for instance business operations,
reputations, information security
and legal and regulatory risk. To
successfully execute the business
strategy, information security plays
a key role in ensuring that strategic
capabilities are securely planned,
developed, and implemented. Strategic
capabilities can include an enhanced
collaboration capability, a virtual
global office capability, or a cloud
computing capability.
Project Objective
This paper aims to understand why
information security must be aligned
with business strategy. Besides, this
study is to illustrate information
security as a platform for protecting
information availability, integrity
and privacy. So, it is crucial to
study the elementary process and to
identify the business aligned security
strategy and technology used.
Information Security Aligned To Enterprise
Management
• The necessary of information
security aligned with business strategy
Business Aligned Security to enterprise
is using strategic activity to implement
business strategy and capabilities
in a secure manner. It is interesting
to note that, most of the organization
uses a risk centric approach to drive
security activities and investment.
Mostly, the risk could be occur through
vulnerabilities, threat and related
risks. Absolutely, The Business Aligned
Security strategy produces improved
outcomes compared to a risk-centric
by using an approach. Cultivating
the current set of mitigating controls
that a risk-centric method entails,
focuses on an important purpose but
it is an operational activity. The
importance of the information technology
is as a significant business function
to achieve benefits to the business
prospects and enable improvement of
company performance to reduce costs,
standardize processes, boost productivity,
improve risk control mechanism, implement
new business strategies and gain competitive
advantage by exploiting new technology.
• Information security management
approach
The best practice approach to utilize
can have a major impact on how security
is perceived by technology users.
The advancement technology to protect
t security from vulnerabilities, threats
and related risk is using technology
well to guide and manage IT services
such as ITIL v3 and depends on how
security controls are technically
integrated with IT services. To do
this, the growth of information technology
is provides several critical conduits
as business information is not to
be compromised and business managers
expect the IT department to achieve
the new vulnerabilities created. However,
there is a boundary to what protection
the IT department can offer without
the entire business approach -the
best firewall in the world will not
stop employees from sending critical
data out of the organization. Therefore,
the role of ISM (Information Security
Management) is taking into consideration
the support and management of business
activities. For example, business
analysis gives maintenance the information
security risk analysis. A sound knowledge
of the enterprise is essential to
support the customization of the greatest
exercise guidance in a suitable and
effective execution that will 'take'
in that particular environment, culture,
business and organizational structure.
Information Security Managers need
to be conscious of the lifecycle of
organizational information assets
and future plans
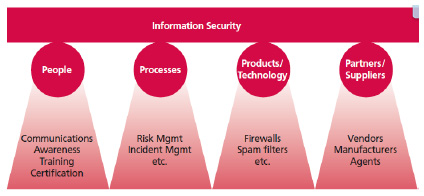
Figure 1: Achieving effective Information
Security Management through the four
Ps
(Clinch, 2009)
and business risk needs to be measured
in order to certify the risks are
evaluated and properly mitigated for
every stage of the lifecycle. The
more successfully it is done, the
more likely the ISM function will
be accepted as lawful for delivering
value to the enterprise. In addition,
the ISM policy and ISMS (Information
Security Management System) should
be developed to ensure the data is
protected for all stages. A useful
perspective of ITIL' four Ps of service
design is shown to explain that the
internal security risk may come readily
to mind and it is likely to underestimate
the security risk arising from organizational
or personal information held, used
or conveyed by partners. Conversely,
the partners only as an entity in
the value network, such as customers,
as well as information accessed by
partners on the organization on IT
system must be safeguarded.
To reach a clear and effective set
of ISM practices, an organization
should follow these steps:
- Create, maintain, distribute and
implement an Information Security
Policy, supported by specific policies
- Recognize the business security
policy and plans
- Understand current and future business
security requirements
- Implement security controls that
support the Information Security Policy
and manage risks associated with access
to services, information and systems
- Document all security controls and
their operation, maintenance and associated
risks
- Manage suppliers and contracts in
respects of access to systems and
services, in conjunction with the
supplier management function
- Manage all security breaches and
occurrences
- Proactively improve security controls
and security risk management
- Ensure security aspects are integrated
into all other ITSM processes.
In order to improve the plan element,
good service level in planned, better
organization of the responsibilities,
well evaluated and implemented. There
is framework which provides five elements
to ensure the creation of an effective
ISM following the Plan-Do-Check- Act
cycle. In this case, ITIL describes
a cycle with the following steps:
Control, P. The framework is shown
below;
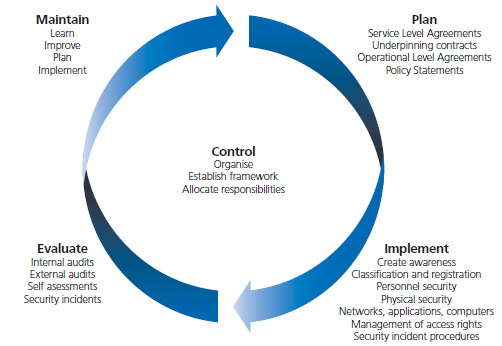
(Clinch, ITIL V3 and Information Security,
2009)
• Manage suppliers and contracts
in respects of access to systems and
services, in conjunction with the
supplier management function
- Manage all security breaches and
occurrences
- Proactively improve security controls
and security risk management
- Ensure security aspects are integrated
into all other ITSM processes.
• The alignment process
• Recognize the type
of business: classify the whole document
for the business process either formally
or informally to realize the both
formal and informal and preferred
outcome from several factors such
as capturing, processing, storing
and distributing information or data.
• Acknowledge the culture:
evaluate the structure, attitude and
nature of the organization.
• Identify the IT state:
recognize all the IT assets, application
and distribution channel, with a realistic
understanding of the nature and culture
in the organization.
• Realize the value chain:
find and document the relationship
or related points between the business
and IT estate.
• Understand the context:
Gather and collate intelligence about
essential factors internal and external.
• Define the change agenda:
examine the context, the business
strategy and powerful factors, recognize
impact and application for the IT
estate.
• Chart the technology
road map: priorities, time line, and
optimize the change agenda.
- Plan the work program: translate
the technology roadmap into business
unit plans.
- Populate the distribution framework:
the overall program of work for sending
information technology to support
business operation.
- Accomplish the business advantages:
implement the delivery framework.
• Advantages of a Business
Aligned Security Strategy
o Security strategy remarkably aligned
with the business strategy
o Adjoining alignment between funded
corporate initiatives and security
initiatives
o Forward-looking security strategy
o Fewer point solutions / more strategic
security initiatives
o Good explanation for finance security
initiatives
o The view of security is raised to
being a strategic enabler
The crucial impact of aligning security
and enterprise are essential to achieve
success for organizations that employ
technology. In addition, the company
also should understand the nature
of several challenges to address such
as it must understand the current
business operation like organizational
culture, Knowledge of the IT estate
resources as well as the value chain,
Good awareness of future business
context and influential factors and
a clear vision as yo where the organization
is going and how to achieve the target
and business goals.
Literature Review
Information technology is a platform
or method for supporting the organization
in achieving its goals and objectives.
However, the technology project may
face potential failure to achieve
its requirements or goals to influence
the risk of business failure against
threats. Thus, the implementation
of business information security in
enterprise management is an ideal
method for operation success. "The
main goal of information security
(IS) is to secure the business against
threats and ensure success in daily
operations, and aid the businesses
in reaching the desired level of reliability
and productivity through ensuring
integrity, availability and confidentiality".
This means to keep information secure;
information security is a platform
for protecting information availability,
integrity, and privacy. The article
of "Business Aligned Security"
by Don Elledge and Roin Nance (2009),
discusses how information security
works within the enterprise. They
figure out the strategy of Business
Aligned Security and risk-based strategies
are not mutually exclusive. In managing
overall risk profile, an organization
has to continue in handling it but
it is not confronting current business
opportunities. In contrast, the security
organization plays an important role
to communicate the security value
of business and its impact. To simplify,
implement Business Aligned Security
approach is interrelating the way
an organization perform its business
activities with information security.
According to "An Executive Field
Manual" by Michael Fey, Brian
Kenyon, Kevin Reardon, Bradon Rogers
and Charles Ross (2012) to explain
the strategic plan refers to required
action that should be taken, and the
impact and the process towards implementing
the action. To simplify, it is an
instrument for measuring and managing
the direction to be in alignment towards
the defined plan. To expound the Business
Model for Information Security began
life as a model for systemic security
management. The model was created
by Dr. Laree Kiely and Terry Benzel
at the USC Marshall School of Business
Institute for Critical Information
Infrastructure Protection. There are
four elements of the model. The first
is Organization Design and Strategy.
An organization refers to the interaction
between an intercommunication of people,
assets and processes to define roles
and undertake a common goal. The goals
to be accomplished are specified by
the enterprise's strategy. Each part
of the strategy is defined by the
people as the second element of the
model to implement it. Next to get
things done, both formal and informal
mechanisms process is included and
provides a vital link to all of the
dynamic interconnections. In implementing
the operational part of the organization
element, the strategy derives progressions
to recognize, measure, manage and
control risk, availability, integrity
and confidentiality as well as to
ensure accountability. To make processes
more effective, the technology element
is composed of all of the tools, applications
and infrastructure. Technology has
its own dynamic risks as it experiences
frequent changes. Given the typical
enterprise's dependence on technology,
technology constitutes a core part
of the enterprise's infrastructure
and a critical component in accomplishing
its mission.
The article "Managing for Enterprise
Security" by Richard A. Caralli
(2004) discusses misaligning business
information security in an enterprise
with strategic drivers bringing undesirable
organization elasticity. This is a
fundamental fact that having large
resources not aimed at affording the
organization's strategic drivers may
not recover the organization's resiliency.
The authors have come up with evidence
their field work has witnessed continuous
failure of organizations to report
improvements in grasping or understanding
clearly the security goals even as
the organizations acquire and execute
advance security technologies. For
example, a new firewall device is
introduced but still results in increase
in risk assessment activity in organizations.
The assessment of organizational risk
as believed by many organizations,
should be performed by IT personnel
considering their responsibility for
security. However, the authors express
their disappointment on the observation
with the CERT® Operationally Critical
Threat, Asset, and Vulnerability Evaluation
SM (OCTAVE®) method as they found
out that the IT personnel who are
among students participating in the
OCTAVE training were unable to give
final decisions on security requirement
of their organizations' important
assets unlike the owner of the asset
which is the business personnel.
Conclusion
The advancement of technology plays
an effective role in enterprises to
maintain profitable, as information
security has become more of a business
enabler than ever thought possible.
The main goal of information security
(IS) is to secure the business against
threats and aid the businesses in
reaching the desired level of reliability
and productivity through ensuring
integrity, availability and confidentiality.
The business needs approaches have
been identified as a holistic approach
which examines the system as a complete
functioning unit and the other approaches
are to examine the whole organization.
The specification of security requirement
is to recognize organizations' requirement
with respect to security. The effectiveness
of business information security should
be aligned with business strategy
through a well defined element process.
The strategy requires the process
element to identify, measure, manage
and handle risk, availability, integrity
and privacy as well as to ensure accountability.
Next, the technology element is composed
of all the tools ,applications and
infrastructure for process efficiency.
References
1. Project Management Institute, A
Guide to the Project Management Body
of Knowledge, (PMBOK Guide), Fourth
Edition, ANSI/PMI 99-001-2008, pp.
273-312.
2. Clinch, J. (2009, May). ITIL V3
and Information Security.9.
3. Clinch, J. (2009, May). ITIL V3
and Information Security. 10.
4. Garvey, P.R., 2008, Analytical
Methods for Risk Management: A Systems
Engineering Perspective, Chapman-Hall/CRC-Press,
Taylor & Francis Group (UK), Boca
Raton, London, New York, ISBN: 1584886374
5. Gustavo Alberto de Oliveira Alves,
"Information Security, An original
vision of Management", Ed. Ciência
Moderna, 2005 (in portuguese).
6. Basie von Solms, "Information
Security Governance e Compliance management
vs operational Management", Computers
& Security, 24, Elsevier, pp.
443-447, 2005.
7. Bharadwaj, A. S. (2000). A resource-based
perspective on information technology
capability and firm performance. An
empirical investigation. . MIS Quarterly,
24(1), 169-196.
8. Scholtz, T. (2013). Seven ways
to align security with the business.
How can security play a central role
in enabling business growth?
9. Bordoloi, C. (2012, 12 19). How
to Align Security with Strategic Business
Objectives. Retrieved October 30,
2014,
http://www.enterprisecioforum.com/en/blogs/cj-bordoloi/how-align-security-strategic-business-ob
10. Kent Anderson, C. (2014). A Business
Model for Information Security. ISACA.
Retrieved 12 01, 2014, from http://www.isaca.org/Journal/Past-Issues/2008/Volume-3/Pages/A-Business-Model-for-Information-Security1.aspx
11. Driving Alignment between business
and security.(2014). Retrieved November
11, 2014, from http://www.edgile.com/what_we_do/strategy_and_governance.html
|